AI-powered security analysis tool

After announcing an AI-powered Copilot assistant for Office apps, Microsoft is turning its attention to Security.
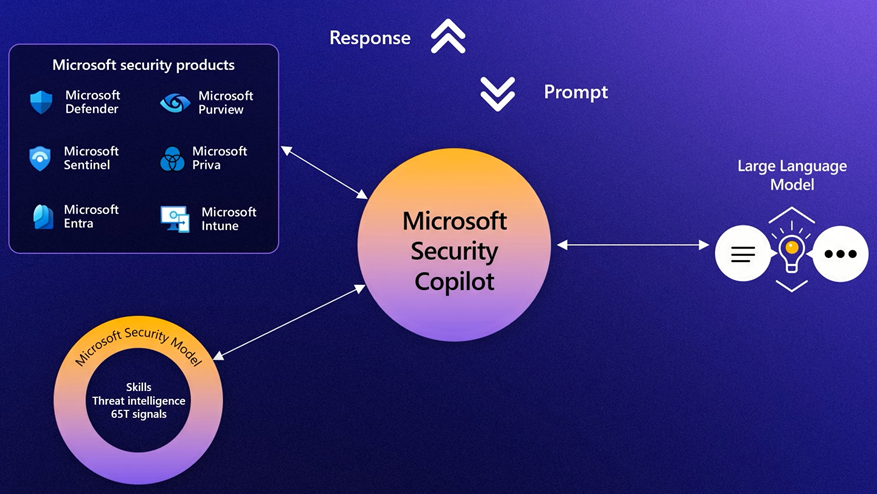
Microsoft Security Copilot is an assistant for cybersecurity teams, design for simply and help company identified and respond security incident in minutes instead hours and days.
The magic behind the scene it’s the Microsoft Copilot system. Copilot is more than OpenAI’s ChatGPT embedded into Microsoft 365 Apps. It’s a sophisticated processing and orchestration engine to combine the power of LLMs (Large Language Models), including GPT-4, with your Microsoft tools and trained models.
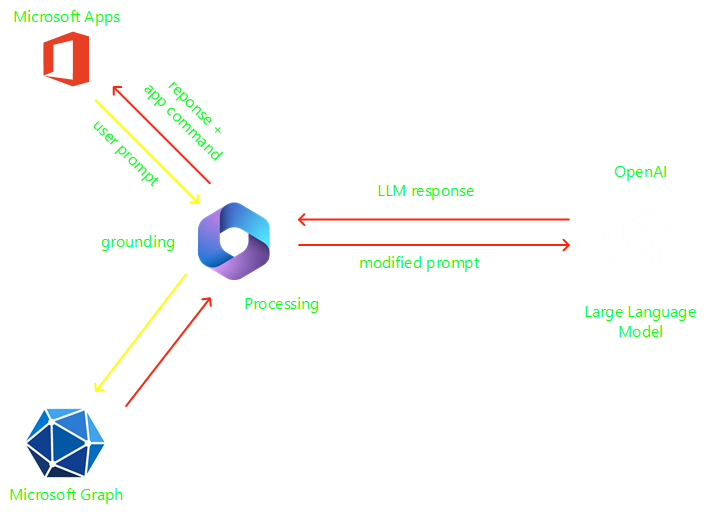
The key to unlocking productivity in business is connecting LLMs to company data, in a secure, compliant, privacy-preserving way.
Copilot is integrated into Microsoft 365 and automatically inherits the company’s valuable security, compliance, and privacy policies. Data leakage is a concern for customers, Copilot System LLMs are not trained on your tenant data or you prompts.
This ecosystem is what makes Microsoft Security Copilot possible. It is designed to assist a security analyst’s work rather than replace it.
Simplify the complex, synthesizing the data from multiple sources into clear, actionable insights and respond to incidents in minutes instead of hours.
Triaging signals at machine speed, surface threats early, and get predicative guidance to help prevent an attacker’s next move.
Addressing the talent gap, helping the team make the most impact and build their skills with step-by-step instructions for mitigating risks.
Microsoft Security Copilot connects the end-to-end security tooling from Microsoft with the copilot technology, using the Microsoft Security Model with security trained skills to improve the prompt before send to LLMs.
Incident response
Identify an ongoing attack, assess its scale, and get instructions to begin remediation based on proven tatctics from real-world security incidents.
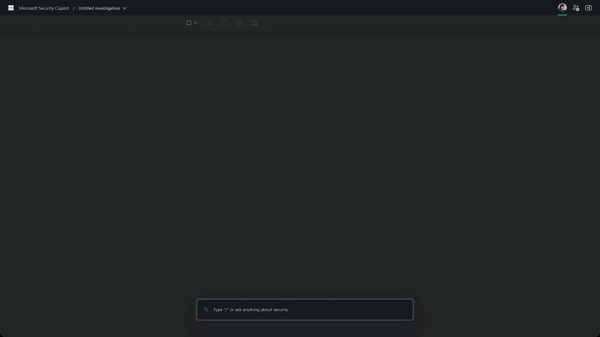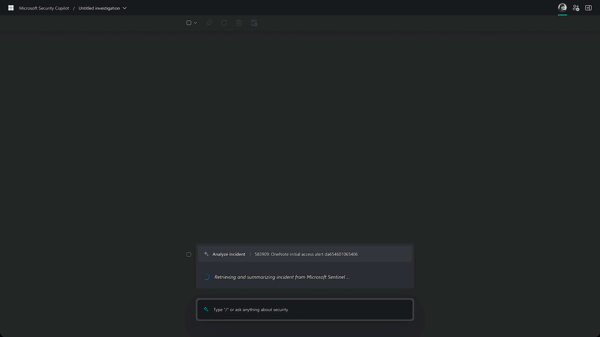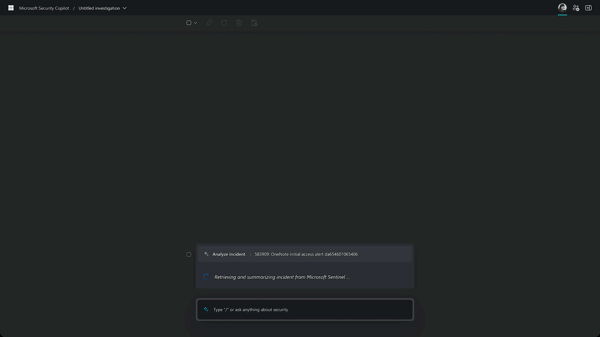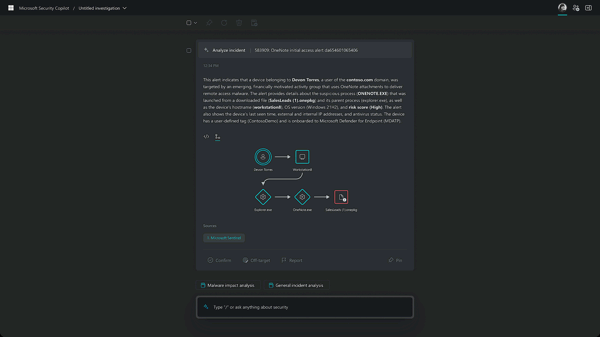
Threat Hunting
Discover whether your organization is susceptible to known vulnerabilities and exploits. Examine the environment one asst at a time for evidence of a breach.
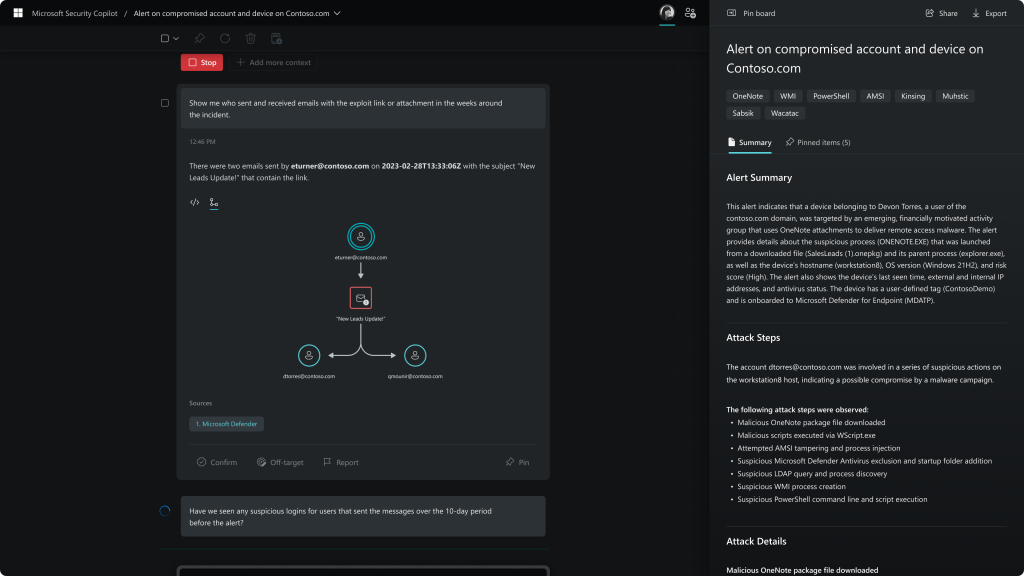
Security Reporting
Summarize any event, incident, or threat in minutes and prepare the information in a ready-to-share, customizable report for your desired audience.
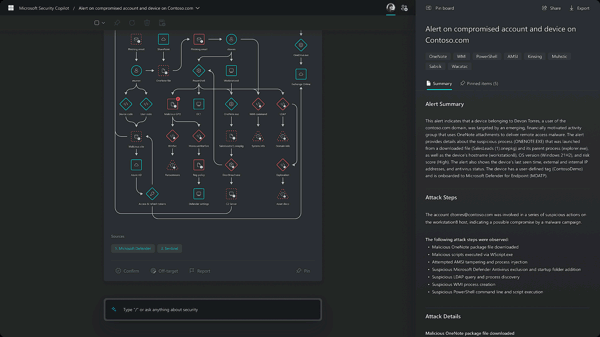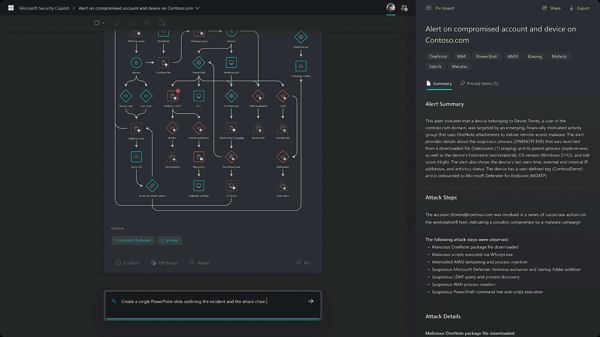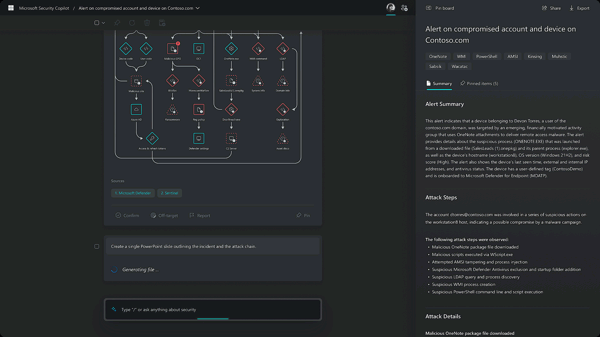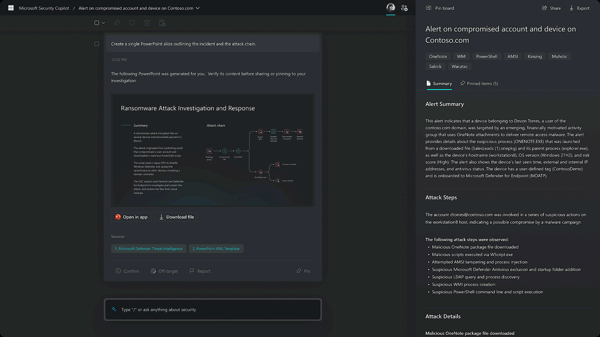
The product is very new, until moment of this article it is in private preview.
Stayed informed, subscribe here to receive information about the product.
Leave a Reply