Cloud Security Tips
In today’s interconnected world, networks serve as the lifeblood of our digital infrastructure. Whether you’re running a robust SAP system or any other workload, whether you are leveraging the flexibility of the cloud or relying on on-premises data centers, the network plays a pivotal role in enabling seamless communication and data exchange. However, as Uncle Ben (Spiderman-Marvel) used to say, with great power comes great responsibility, especially when it comes to network security.
Imagine the network as a bustling metropolis, where data flows through intricate pathways connecting various components of your environment. Just like in a city, ensuring the safety and security of this network is paramount. While networks enable accessibility and convenience for users, they can also become breeding grounds for malicious threats. Like an infectious virus spreading between individuals, a compromised network can propagate vulnerabilities and jeopardize the integrity of your entire infrastructure.
In this post, we will dive into the fascinating world of Azure Network Management capabilities, combining insights from Microsoft CAF (Cloud Adoption Framework) and Azure Well-Architect recommendations with my expertise in cloud environments and security.
Hub-Spoke Topology
A hub-spoke topology, also known as a hub-and-spoke architecture, is a networking design pattern where multiple branches or spoke sites are connected to a central hub site. In this topology, all communication between the spoke sites is routed through the central hub. This creates a hierarchical network structure where the hub acts as a central traffic controller.
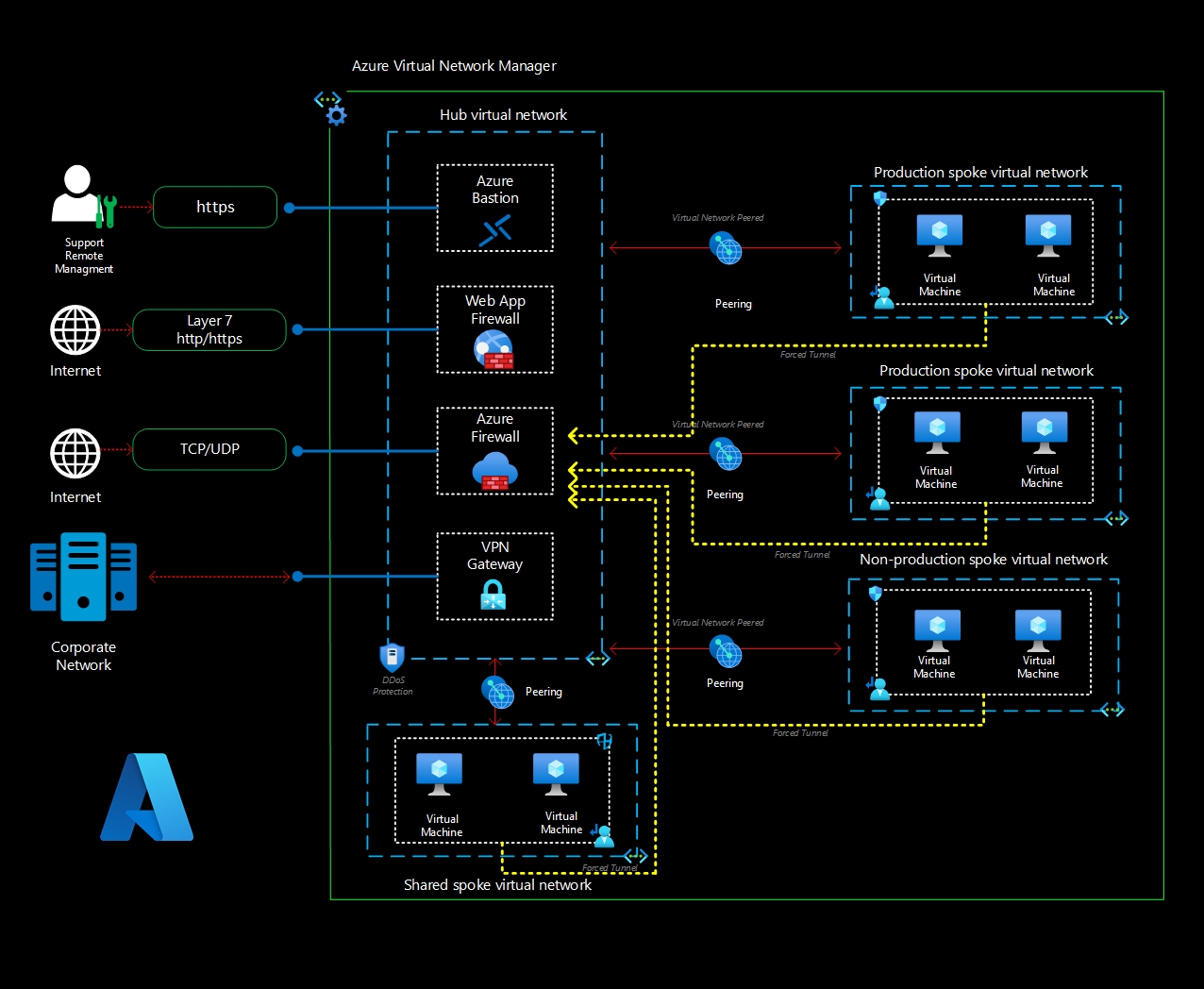
Hub virtual network is hosted shared Azure Services.The hub virtual network is the central point of connectivity between spokes and cross-premises networks.
Spoke virtual networks these virtual networks are used by the workloads. Each workload can include multiple tiers, with multiple subnets connected. Spokes can exist in different subscriptions and representing differents environemnts, such as Production or Non-production.
Communication trough an Firewall
In this particular network topology, all communication between the spokes goes through a firewall, such as Azure Firewall or a Network Virtual Appliance(NVA). The purpose of this configuration is to filter and secure the communication.
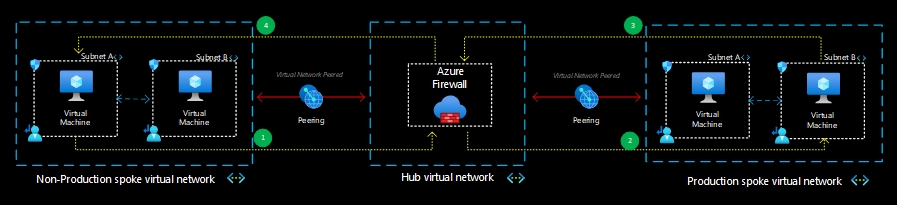
The peering process establishes a logical connection between the two spokes and the hub’s network. This connection enables data transfer and connectivity between these components.
When it comes to communication between subnets, there are two possible approaches. One option is to use the internal routing provided by Azure Network, allowing direct the communication between subnets.Alternatively, the traffic can be routed through the filtered hub and then directed back to the destination subnet. However, it’s important to note that for SAP environments, this routing method is not recommended due to potential latency issues, especially when communicating between the application and the database.
To address this, it is advisable to carefully consider and control the routing and authorization of traffic between production and non-production resources, as well as SAP and Non-SAP resources. To manage this, Network Security Groups (NSGs) can be utilized. NSGs play a crucial role in regulating network traffic by specifying rules and policies that determine how data flows between different subnets. Further details on the function and operation of NSGs will be explained bellow.
Enterprise Connectivity
Azure Enterprise Connectivity refers to the capabilities and services provided by Azure to establish secure and reliable connectivity between on-premises networks and Azure cloud resources. It enables organizations to extend their network infrastructure into Azure, facilitating seamless integration of on-premises and cloud environments.
Azure Virtual Network allows you to create isolated and customizable network environments in Azure. It serves as the foundation for establishing connectivity between your on-premises network and Azure resources.
Azure Private Endpoint is a networking feature that allows you to securely access Azure services privately from within your Azure virtual network (VNet). It provides a private IP address within your VNet that serves as an entry point to access specific Azure resources without using public IP addresses or traversing the public internet.
Azure Virtual Network Gateway is a networking component that enables secure connectivity between your on-premises network and Azure virtual networks. It supports Virtual Private Network (VPN) connections and ExpressRoute connections to establish encrypted and dedicated connectivity options.
Azure VPN Gateway provides a secure, encrypted connection between your on-premises network and Azure virtual networks over the public internet. It allows you to create site-to-site VPN connections or point-to-site VPN connections, depending on your connectivity requirements.
Azure ExpressRoute offers a private and dedicated connection between your on-premises network and Azure through a connectivity provider. It provides a higher level of security, reliability, and performance compared to VPN connections by establishing a direct, private connection over a network service provider.
This enables hybrid scenarios, seamless data transfer, and integrated operations between on-premises and cloud environments, empowering businesses to leverage the benefits of Azure while maintaining the necessary connectivity and security requirements.
Firewall on Azure
Azure has many choices of firewall, depends on your specific requirements and the level of control and functionality you need for your network security. Azure Firewall is a native azure service that provides comprehensive network-level security.
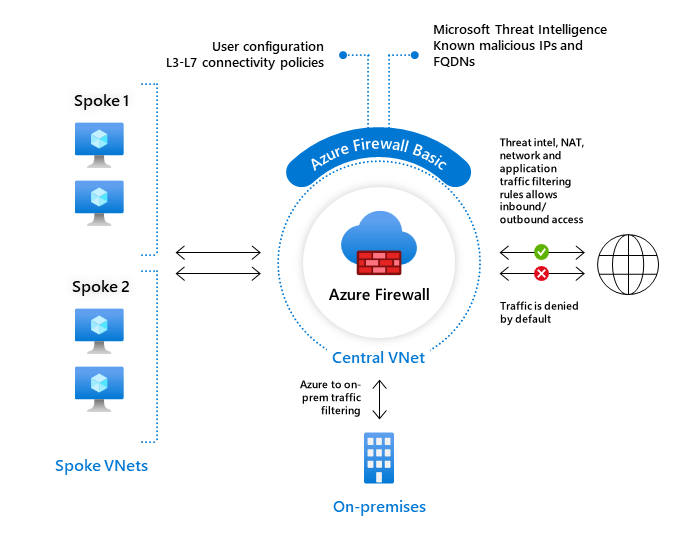
Source: Internet
Here are some features and capabilities of Azure Firewall:
- Network-level filtering: Azure Firewall filters both inbound and outbound traffic based on source and destination IP addresses, ports, and protocols.
- Application-level filtering: It allows you to create application rules to allow or deny traffic based on specific application protocols, such as HTTP, HTTPS, and SQL.
- Network Address Translation (NAT): Azure Firewall includes NAT capabilities, allowing you to translate private IP addresses to public IP addresses for outbound traffic.
- High availability: The solution is designed for high availability with built-in auto scaling and automatic failover, ensuring continuous network protection.
- Integration with Azure services: It seamlessly integrates with other Azure services like Azure Monitor for logging and analytics, Azure Sentinel for security information and event management (SIEM), and Azure Virtual WAN for centralized firewall management.
- Outbound internet connectivity for private networks: It provides outbound internet connectivity for virtual networks that use private IP address ranges, allowing resources within the virtual network to access the internet securely.
Azure Firewall is available in three versions, Basic, Standard, and Premium. In the version Premium, according to Microsoft Documentation these are the features available.
- TLS Inspection: protocol primarily provides cryptography for privacy, integrity, and authenticity using certificates between two or more communicating applications.
- IDPS: A network intrusion detection and prevention system (IDPS) allows you to monitor network activities for malicious activity, log information about this activity, report it, and optionally attempt to block it.
- URL filtering: extends Azure Firewall’s FQDN filtering capability to consider an entire URL along with any additional path. For example, www.contoso.com/a/c instead of www.contoso.com.
- Web categories: administrators can allow or deny user access to website categories such as gambling websites, social media websites, and others.
Overall, Azure Firewall is an effective solution for securing and monitoring network traffic in your Azure environment, providing centralized control and protection for your virtual network resources.
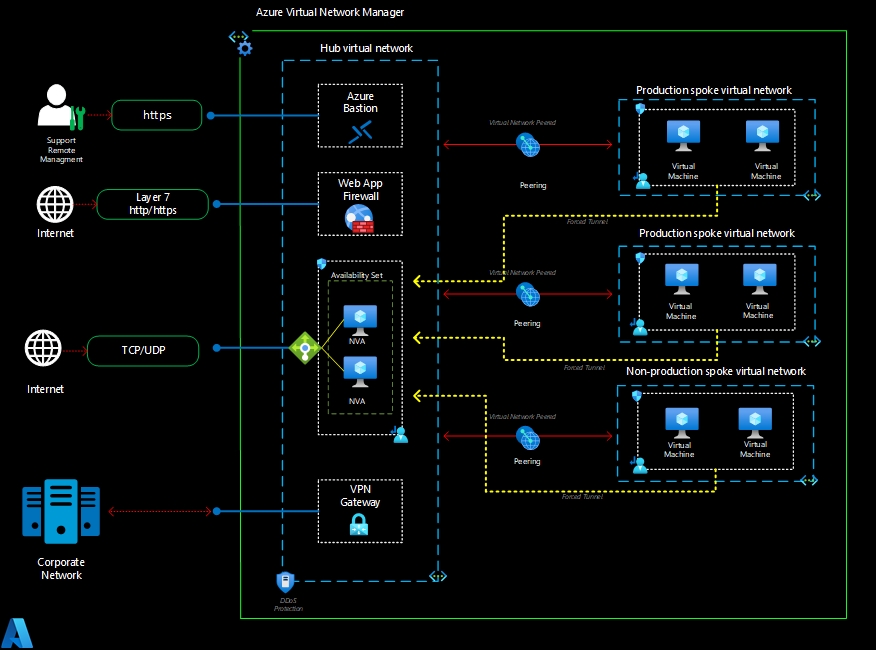
Other option it is running an Network Virtual Appliance (NVA) on Azure allows you to deploy third-party firewall or routing solutions to enhance network security and control in your environment. An NVA is a virtual machine or a virtual appliance that provides advanced network functionalities, currently Palo Alto, Checkpoint, Fortinet, Cisco, and others are available in the Azure Marketplace. Regarding the licenses, you can bring your own licenses (BYOL) or some appliances you have option to pay for the use (PYG).
Azure Network Security Group (NSG) is a fundamental network security feature provided by Azure that allows you to filter and control network traffic to and from Azure resources. NSGs provides a level of network security by enabling you to define rules that permit or deny inbound and outbound traffic based on some criteria such as source and destination IP addresses, ports, and protocols.
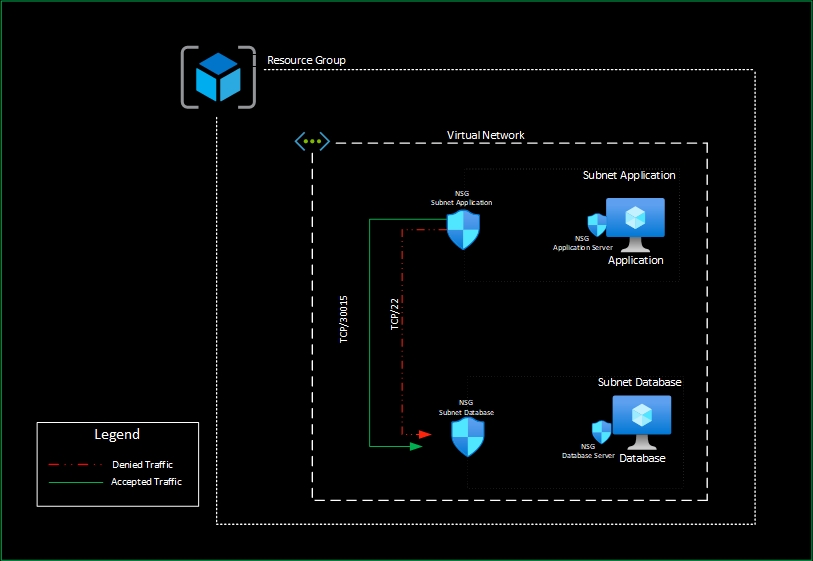
By leveraging Azure NSGs effectively, you can enforce network traffic control and implement basic network security measures to protect your Azure resources and application. However, I preferer to use NSGs for small environments or for controlling the traffic between subnets of the same workload. For example, avoiding to send the traffic from application to database through the firewall.
Application Security Group
Azure Application Security Groups (ASGs) are a networking feature that helps simplify network security management for Azure virtual machines (VMs). ASGs allow you to group VMs based on their application tiers or security requirements and apply network security rules to the group as a whole, rather than individual VMs.
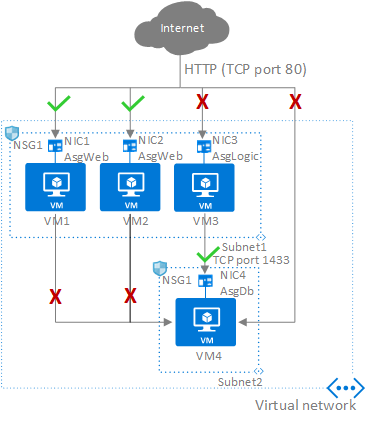
Source: Internet
Here are key features and capabilities of this solution:
- Simplified Rule Management: provide a logical grouping mechanism that simplifies the management of network security rules. Instead of configuring rules individually for each VM, you can define rules at the ASG level, making it easier to manage and maintain network security policies.
- Granular Network Security: can be used in conjunction with Azure Network Security Groups (NSGs) to define granular network security rules. NSGs allow you to control inbound and outbound traffic to your VMs based on IP addresses, ports, and protocols. By associating ASGs with NSG rules, you can apply those rules to all VMs within the ASG.
- Grouping Based on Application Tiers: ASGs are commonly used to group VMs based on application tiers, such as web servers, application servers, and database servers. By associating VMs with their respective ASGs, you can define and enforce specific network security rules for each tier, ensuring appropriate access control and network segmentation.
- Dynamic Membership: It support dynamic membership, allowing you to add or remove VMs from the group without modifying the network security rules. This flexibility simplifies scalability and management, particularly in scenarios where VMs are dynamically provisioned or decommissioned.
- Cross-Subnet Communication: can span multiple subnets within the same virtual network. This allows you to define network security rules that govern communication between different application tiers across subnets, providing a flexible and secure architecture for your applications.
- Integration with Azure Services: ASGs can be used in conjunction with other Azure services, such as Azure Load Balancer, Azure Application Gateway, and Azure Firewall. This enables you to define network security policies that align with the requirements of these services and ensures secure communication and traffic flow within your Azure infrastructure.
By leveraging Azure Application Security Groups, you can simplify network security management, enforce granular security policies, and improve the scalability and agility of your Azure VM deployments.
Web Application Firewall
Azure Web Application Firewall (WAF) is a cloud-based service provided by Azure to protect web application from common web-based attacks and vulnerabilities. It helps safeguard your web applications by providing a layer of security between your application and the internet.
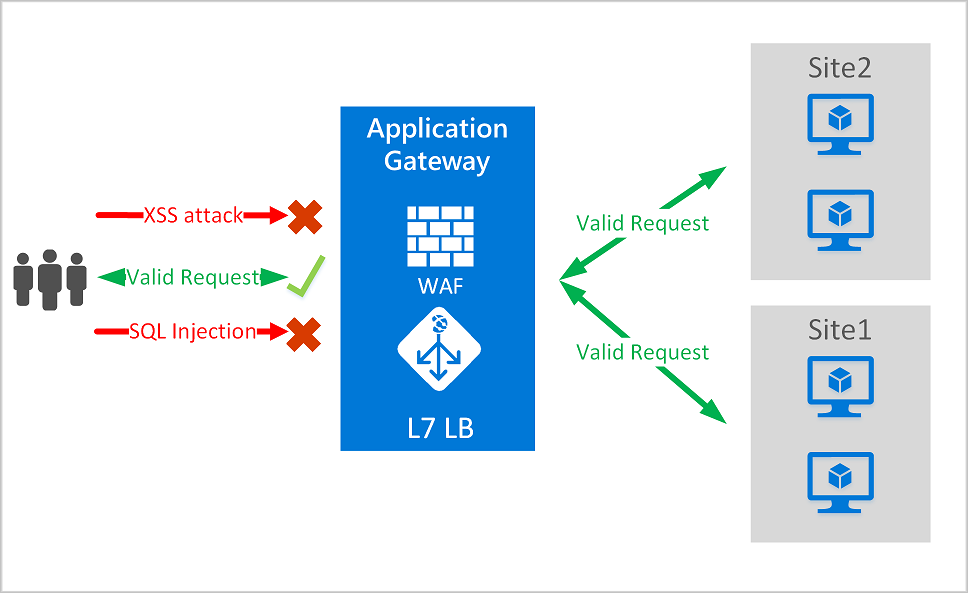
Source: Internet
Here are key features and capabilities of Azure Web Application Firewall:
- Web Application Protection: It uses a combination of rule sets and machine learning algorithms to detect and block malicious traffic targeting your web applications. It protects against attacks such as SQL injection, cross-site scripting (XSS), remote file inclusion, and more.
- Web OWASP Core Rule Set (CRS): Azure WAF leverages the OWASP CRS, a widely used rule set developed by the Open Web Application Security Project (OWASP). This rule set contains a comprehensive set of rules to detect and mitigate common web application vulnerabilities.
- Custom Rules: In addition to the OWASP CRS, Azure WAF allows you to create custom rules to address specific security requirements of your web applications. Custom rules enable you to define granular protections and customize the behavior of the WAF based on your application’s unique needs.
- Bot Protection: Azure WAF includes bot protection capabilities to detect and mitigate automated bot traffic targeting your web applications. It helps prevent attacks such as credential stuffing, content scraping, and account takeover.
- Monitoring and Logging: It provides logging and monitoring capabilities, allowing you to gain visibility into web traffic, security events, and potential threats. It integrates with Azure Monitor, Azure Security Center, and Azure Sentinel for centralized monitoring and analysis of security events.
It is important to note the Azure Web Application Firewall is a solution that can associated with three web application solutions:
- Azure Application Gateway: is a web traffic load balancer that enables you to manage traffic to your web applications.
- Azure Front Door: is Microsoft’s modern cloud Content Delivery Network (CDN).
- Azure CDN: ) is a distributed network of servers that can efficiently deliver web content to users.
Azure WAF is a layer 7 protection solution focused on web application security. It complements other network-level security measures such as Azure Firewall and Network Security Groups (NSGs) to provide a comprehensive security posture for your applications.
Azure DDoS
Azure provides Distributed Denial of Service (DDoS) protection services to help safeguard your applications and infrastructure from DDoS attacks. Azure DDoS Protection is a built-in service that provides defense mechanisms to mitigate and minimize the impact of DDoS attacks.
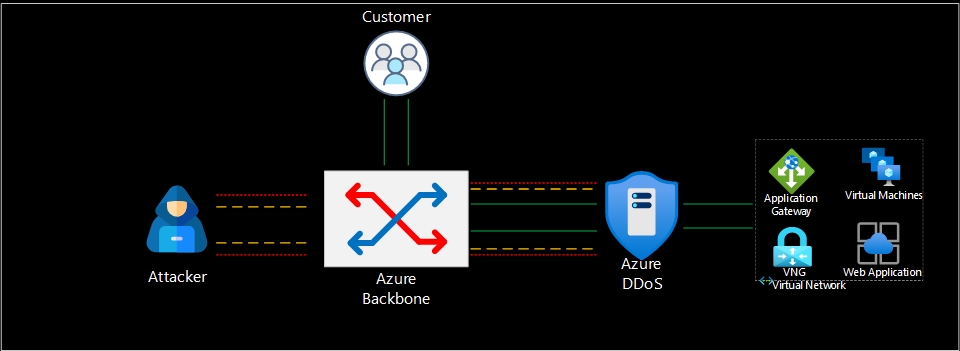
Here are key aspects of Azure DDoS Protection:
- Network DDoS Protection: Azure automatically provides baseline DDoS protection for all public IP addresses associated with resources deployed in Azure. This protection is provided at the Azure network edge, where traffic is monitored and analyzed to identify and mitigate DDoS attacks.
- Traffic Monitoring and Analysis: Azure DDoS Protection continuously monitors network traffic to identify patterns indicative of a DDoS attack. It leverages machine learning algorithms and threat intelligence to detect and mitigate attacks in real-time.
- DDoS Mitigation: ) When a DDoS attack is detected, Azure DDoS Protection uses various mitigation techniques to minimize the impact on your applications and infrastructure. This includes traffic filtering and rate limiting to block malicious traffic and ensure legitimate traffic can reach your resources.
- Application Layer DDoS Protection: ) In addition to network-level protection, Azure also offers application layer DDoS protection through Azure DDoS Protection Standard. This enhanced protection service provides additional mitigation capabilities specific to application layer attacks, such as HTTP/S protection and protection against volumetric attacks targeting specific application endpoints.
- Traffic Insights and Reporting: ) Azure DDoS Protection provides insights and reporting capabilities to help you understand DDoS attack trends, traffic patterns, and the effectiveness of the protection. This allows you to analyze and optimize your DDoS mitigation strategies.
It’s important to note that while Azure DDoS Protection provides automatic baseline protection for all public IP addresses, you can further enhance your protection by opting for Azure DDoS Protection Standard. This premium tier offers advanced features, including higher mitigation thresholds, increased protection for virtual network resources, and enhanced application layer protections. By leveraging Azure DDoS Protection services, you can mitigate the risk of DDoS attacks and ensure the availability and performance of your applications and services deployed on Azure.
Azure Bastion
Azure Bastion is a fully managed service provided by Azure that offers secure and seamless remote access to Azure virtual machines (VMs) over the Secure Shell (SSH) or Remote Desktop Protocol (RDP) protocols. It eliminates the need to expose VMs to the public internet or maintain separate jump hosts or VPN connections for remote access.
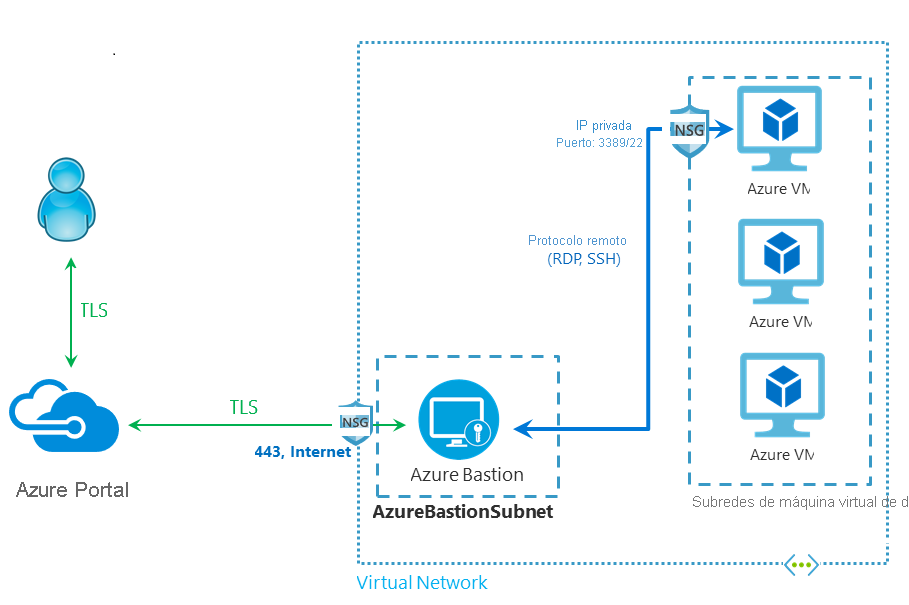
Source: Internet
Azure Bastion simplifies and secures the remote management of Azure VMs, providing a centralized and secure way to access your virtual machines without exposing them to the public internet. It enhances security, reduces administrative overhead, and improves the overall management experience for accessing Azure VMs remotely.
Azure Network Watcher
Azure Network Watcher is a monitoring and diagnostics service provided by Microsoft Azure. It helps you monitor, diagnose, and gain insights into your Azure network infrastructure. Network Watcher provides a set of tools and capabilities to analyze network traffic, troubleshoot connectivity issues, and monitor network performance.
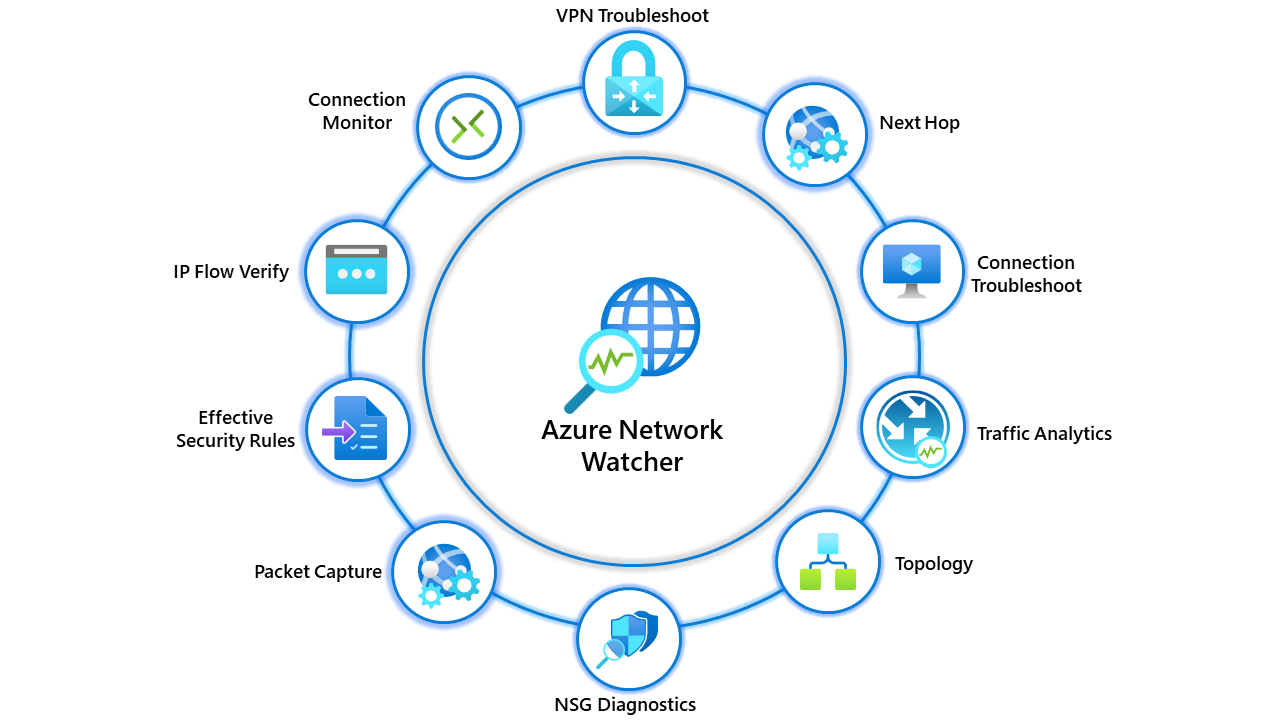
Source: Internet
Traffic Analytics, a feature of Network Watcher, provides visibility into network traffic patterns and flow across your virtual networks. It helps you identify and analyze traffic flows, detect anomalies, and gain insights into the sources and destinations of network traffic.
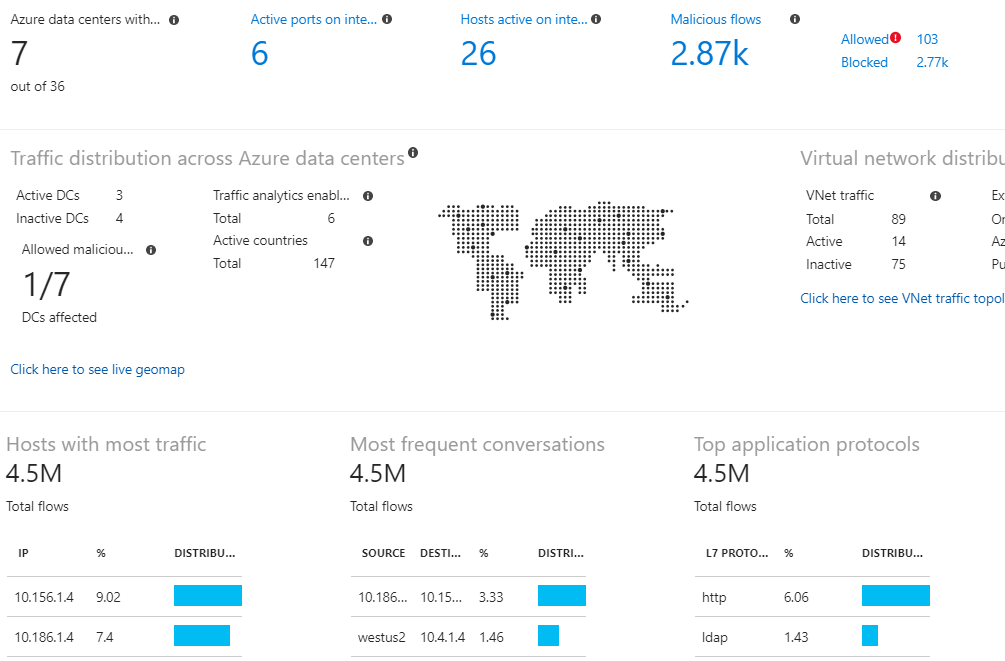
Source: Internet
Azure Network Watcher is a powerful tool that empowers network administrators and operators to effectively monitor, troubleshoot, and optimize their Azure network infrastructure. With Network Watcher, you can proactively identify and resolve network issues, ensuring smooth operations and reliable connectivity. By gaining insights into network performance metrics, such as latency and packet loss, you can fine-tune your network configuration and enhance overall performance.
Additionally, Network Watcher provides robust security features, including traffic analytics and security group analysis, enabling you to strengthen network defenses and protect against potential vulnerabilities. With its comprehensive set of tools and capabilities, Azure Network Watcher is an indispensable resource for network management, helping you maintain a secure, efficient, and reliable Azure network environment.
Next Post
While it’s not possible to cover all the possibilities of Azure’s network core in a single post, I was able to provide an overview of its capabilities and the importance of designing an efficient and secure network topology. In the next post, we will discuss the encryption options available in Azure to protect our data in transit, at rest, and in use, further enhancing the security of our infrastructure.
Leave a Reply