Cloud Security Tips

In today’s digital world, where data breaches and privacy concerns are on the rise, encryption plays a crucial role in safeguarding sensitive information. Encryption is the process of converting plain, readable data into a coded form using complex and security algorithms. It ensures that only authorized individuals can access and understand the data.
This article offers a comprehensive overview of the utilization of encryption within Microsoft Azure. It delves into the key aspects of encryption, encompassing encryption at rest, encryption in transit, and efficient key management practices.
Let’s begin understanding the differences between encryption at use, at rest and in transit.
Encryption in use refers to the encryption of data while it is actively being processed or used by applications or system. This find of encryption focuses on protecting data while it is in memory or being processed by applications, databases, or other computing system. The purpose of encryption in uses is to safeguard sensitive data from unauthorized access or disclosure during active usage.
Encryption at rest refers to the process of encrypting data when it is stored or “at rest” in storage devices or system. This ensures that even if unauthorized individuals gain physical access to the storage media or compromise the storage system, they will not be able to access or decipher the data without the encryptions keys.
Encryption in transit refers to the practice of securing data while it is being transmitted or sent over a network. When data is sent from one device to another, such as over the internet or a local network, it can be intercepted by malicious actors. Encryption in transit ensures that even if the data is intercepted, it remains unreadable and protected. The most common protocols for securing web traffic for instance is Transport Layer Security (TLS), this protocol provides secure communication over a network by encrypting data and authenticating the parties involved in the communication.
Microsoft Azure provides multiple methods for securing data in a client-server infrastructure. Now, let’s delve into some specific concepts to gain a better understanding.
Client-Side Encryption this is performed outside of Azure. It’s include:
- Data encrypted by an application that’s is running in your datacenter or by a service application.
- Data is already encrypted when it is received by Azure.
With client-side encryption, generally cloud service providers don’t have access to the encryption keys and cannot decrypt this data.
Server-Side Encryption this is performed inside of Azure. Refers to the encryption of data at rest within Azure Services. It provides an additional layer of security by encrypting the data stored in multiples Azure Services, such as Azure Storage, Azure SQL Database, Azure Cosmos DB, and more.
Azure has three server-side encryption models offer different key management characteristics, which you can choose according to your requirements.
- Service-managed keys: this model provides a balance between control and convenience with minimal administrative overhead. Azure manages the encryption leys on your behalf, ensuring secure data storage without the need for key management on your part.
- Customer-managed keys: with this model, you have control over the encryption keys. You can bring your own keys(BYOK) or generate new ones within Azure Key Vault (We’ll cover later). This approach allows you to have more granular control over key management and offers increased security.
- Service-managed keys in customer-controlled hardware:known as Host Your Own Key(HYOK), enables you to manage keys in your proprietary repository outside of Microsoft’s control. It provides the highest level of key control, not all Azure services support this model.
By understanding these server-side encryption models, you can make an informed decision based on your specific needs for key management and control over your data.
Encryption of data in transit

Whenever your Azure traffic moves between Microsoft Azure Datacenters is encrypted by Data-link Layer encryption. This approach is a security measure that provides encryption and decryption services at the data-link layer of a network protocol stack. It aims to protect data as it is transmitted between network nodes by encrypting the contents of data-link layer frames.
The packets are encrypted on the device before being sent, preventing physical “man-in-the-middle”(when a malicious third party intercepts and alters communication betweens two parties without their knowledge or consent) or snooping attacks.
All of outside physical boundaries traffic is not controlled by Microsoft, however Azure offers many mechanisms for keeping data private as it moves from one location to another.
- TLS Encryption: Microsoft gives to you the ability to use TLS protocol to protect data when it’s traveling between Azure cloud service and your services. Microsoft datacenters negotiate a TLS connection with client systems that connect to Azure Services.
- Storage Transactions: all storages trasanctions using Azure services take place over HTTPS. You are able to using REST API over HTTPS to interact with Azure Storages. The Shared Access Signatures(SAS),are tokens that grant limited and time-limited access permissions to specified resource Azure cloud service, including option to specify that only HTTPs protcols can be use with SAS.Regarding Azure Files shares, SMB 3.0 suports encryptions, and it’s avaialable for a few opeating systems.
- Azure VPN encryption: you are able to connect through a corporate or private network creating a secure tunnel to protect the privacy of the data being sent across network. Azure VPN Gateway helps you to send encrypted traffic between your Azure networks and your corporate network accross public connection, or even to send traffic between virtual networks inside Azure if you business required that.
Site-to-Site VPNs use IPSec for transport encryption. Azure VPN gateways use a set of default porposals. It allow you configure VPN using a custom IPSec/IKE policy with cryptographic algorithms and key strengths.
Also Azure can provide a Point-to-Point VPNs allowing individual client computers access to an Azure virtual network. Using SSPT (Secure Socket Tunneling Protocol) to create the VPN tunnel. It can transverse firewalls, because of the tunnel is over HTTPS layer.
One thing important to highlight it is regarding Express Routes, the express routes, are hybrid connection between your corporate network with Microsoft cloud over a private connection with to help of third party provider. This communication it’s not encrypted by itself, if you want to encrypted this traffic an Azure VPN Gateway is needed. So, into the private connection, you’ll have a IPSec tunnel encrypting the traffic.
Encryption of data at rest with Azure Virtual Machines
Azure Virtual Machines provide various options for encrypting data at rest to ensure the security and confidentiality of your data. There are several types of encryption available for your managed disks, here we have it:
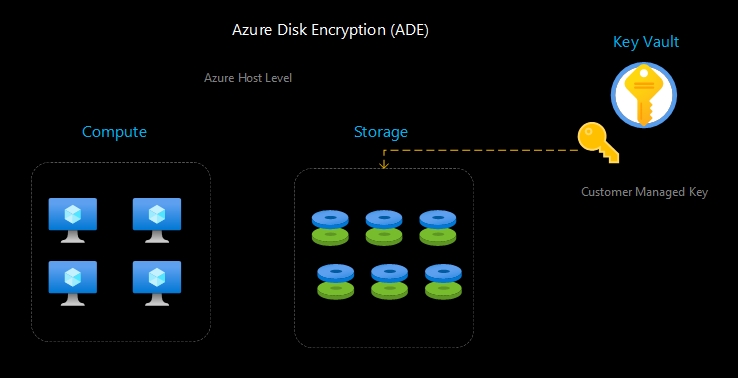
- Azure Disk Storage Server-Side Encryption: is always enabled and automatically encrypts data stored on Azure Managed disks (OS and Data) when persisting on the storage clusters.It is not supported for temp and encryption of caches.
- Azure Disk Encryption: helps protect and safeguard your data to meet your organizational secuirty and compliance commitments. ADEs provides encryption using Bitloker for Windows VMs and DM-Crypt for Linux VMs.
- BitLocker Encryption: is a full-disk encryption fetaure provided by Microsoft Windows. It encrypts the entire operating system disk and any data disks attached to the virtual machine. BitLocker uses the AES(Advanced Encryption Standard) encryption algorithm in XTS mode. Also, Trusted Platform Module (TPM) use is supported.
- DM-Crypt Encryption: is a transparent disk encryption subsystem in Linux. It provides block device encryption and operates at the block level, encrypting the data stored on the disks. DM-Crypt uses various encryption algorithms such as AES, Twofish, Serpent, etc., with a combination of cipher modes like XTS, CBC, etc. The encryption keys are managed by the Linux kernel’s cryptographic subsystem.
- Encryption at host: is a feature that provides additional security for data at rest within Azure Virtual Machines (VMs). With Azure Encryption at Host, the data on the VM’s disks is automatically encrypted by Microsoft at the hypervisor level before it is persisted to the underlying storage.
- Confidential disk encryption: binds disk encryption keys to the virtual machine’s TPM and makes the protected disk content accessible only to the VM. The TPM and VM guest state is always encrypted in attested code using keys released by a secure protocol of bypasses the hypervisor and host operating system. This option currently only available for the OS disk. Encryption at host may be used for other disks on a confidential VM in addition to Cofidential Disk Encryption.
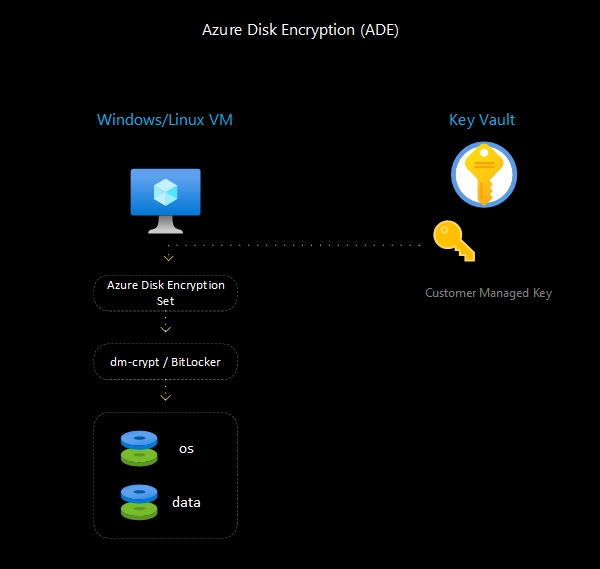
The encryption keys used for Azure Disk Encryption are managed and stored securely within Azure Key Vault, providing an additional layer of security.
Encryption of data at rest with Azure SQL services/mark>
Azure SQL services provide several encryption options to secure data at rest. Here are the encryption features available for Azure SQL:
- Transparent Data Encryption: is a feature that automatically encrypts the database files at rest. TDE performs real-time encryption and decryption of the database, log files, and backups. It uses a Database Encryption Key (DEK) that is protected by a certificate stored in Azure Key Vault or by a service-managed certificate. TDE helps protect against unauthorized access to the database files if they are compromised.
- Always Encrypted: is a feature that enables encryption of specific columns within a database, ensuring sensitive data remains encrypted both at rest and in transit. With Always Encrypted, the data is encrypted by the client application before it is sent to the database, and only the client application has access to the encryption keys. This ensures that sensitive data is never visible in plaintext to database administrators or other users with access to the database.
- Transparent Data Encryption with Bring Your Own Key (TDE with BYOK):TDE with BYOK extends the capabilities of TDE by allowing you to bring and manage your own encryption keys using Azure Key Vault. With TDE with BYOK, you have full control over the encryption keys used for TDE, providing an additional layer of security and control.
By utilizing these encryption features, you can ensure that your data stored in Azure SQL services remains protected and confidential at rest. It’s important to carefully evaluate and choose the encryption options that best align with your security and compliance requirements.
Storing the keys and certificates
Azure Key Vault plays a crucial role in securing sensitive information and cryptographic assets within the Azure ecosystem. Azure Key Vault is a cloud-based service provided by Microsoft Azure that allows you to securely store and manage cryptographic keys, secrets, and certificates. It acts as a central repository for managing and safeguarding your sensitive information used for authentication, encryption, and other security purposes.
- Key Management: Azure Key Vault enables you to create, import, and manage cryptographic keys used for encryption, decryption, signing, and verification. It supports various key types, including RSA, AES, and Elliptic Curve Cryptography (ECC). Key Vault helps ensure the secure storage and lifecycle management of your keys.
- Secret Management: Key Vault allows you to securely store and manage secrets such as passwords, connection strings, API keys, and other sensitive information. Secrets can be accessed programmatically or through the Azure portal, and access policies can be defined to control who can read or manage the secrets.
- Certificate Management: Azure Key Vault provides a secure and scalable way to manage X.509 digital certificates. You can import or generate certificates within Key Vault and use them for SSL/TLS encryption, code signing, and other security scenarios. Key Vault can also automate the renewal and rotation of certificates.
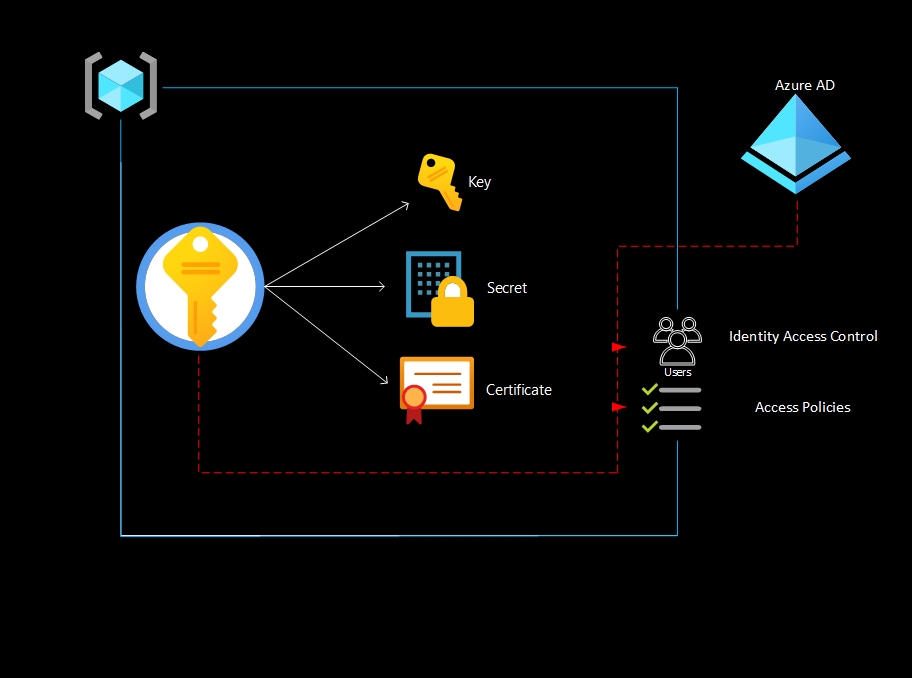
Key Vault seamlessly integrates with other Azure services, such as Azure Virtual Machines, Azure Functions, Azure App Service, Azure Logic Apps, and more. This integration enables you to securely retrieve secrets and keys from Key Vault without exposing them in your code or configuration files.
Key Vault offers granular access control through Azure Active Directory (Azure AD) integration. You can define fine-grained permissions and roles to control who can manage and access the keys, secrets, and certificates. Key Vault also provides audit logs that track all management and data plane operations, helping you meet compliance and regulatory requirements.
Next post
In conclusion, encryption is essential for safeguarding sensitive data by transforming it into an unreadable form, ensuring confidentiality, meeting compliance requirements, mitigating risks of data breaches, maintaining data integrity, and building trust with stakeholders. Encryption is a fundamental security practice that helps protect data at rest, in transit, and in use, playing a crucial role in maintaining the privacy and security of valuable information.
In the next article, I will cover a topic that always generates much discussion: hardened images, the available options, and how to use automation to achieve this goal. And of course, what Azure can offer us.
Leave a Reply