Cloud Security Tips

SAP and Microsoft have a long history of working togheter in a strong partnership that has mutual benefits for their customers. You can run SAP workloads on the Azure platform using different Azure Virtual Machines (Azure VMs) offerings and others Azure Resources such as storages, automation services, and etc.
SAP workloads have always demanded a lot of security needs and sometimes they are not fully addressed, my idea is in this sequence of posts to give some security tips for this type of workloads.
All concepts here are founded on Microsoft Azure documentation such as Microsoft Cloud Adoption Framework, Azure Well-Architected Framework, Sap adoption – Microsoft Cloud Adoption Framework, and least, my experienced in securing cloud environments.
The concepts here can be applied to different cloud providers, the answer is yes, however the provider’s frameworks need to be consulted, as some technologies presented here may be different an AWS or GCP.
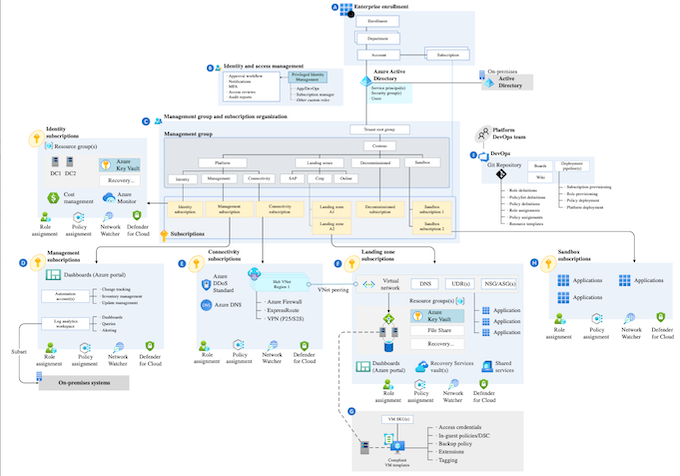
What is the Azure Landing Zone?
A landing zone is an environment for hosting your workloads. An Azure Landing Zone is a well-architected, multiple subscription Azure environment that is scalable and secure.
It’s provides a stable place for your workloads to run a framework to scale, it’s like building a home, you need to correct blueprint and a solid foundation.
You can use this architecture as a starting point. This is only a reference, you should adapt according to business and requirements.
To embrace scalability, it’s suggested follow these five key principles when you are building your landing zone.
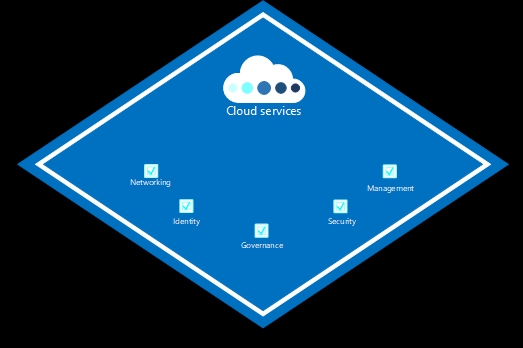
Networking
Network topology and connectivity are fundamental for organizations that are planning their landing zone design. Generally, networking is central to almost everything inside the landing zone. It enables connectivity between your workloads, external users, and your on premises environments.
Identity
Identity provides the basis for a wide variety of security assurance. It’s grants access based on identity authentication and authorization controls in cloud services.Access controls protects data an resources and helps decided which requests should be permitted or not.
Consider the following identity and access management for your landing zone deployments. Based on the following recommendations:
Managed Indentities evalute using for Azure Resources that don’t have need to use credentials. Nowadays, there two options for managed identities system-assigned and user-assigned.
Role-based access control (RBAC), is an authorization system built ARM (Azure Resource Manager) that provides fine-grained access management to Azure resources.
Azure Active Directory and hybrid identity, a critical design decision for enterprise organizations adopting Azure is whether to extend current on-premises identity domains into Azure or create new identity domains.
Azure AD Privileged Identity Management to establish zero-trust and least privilege access. Map your organization’s roles to the minimum access levels needed.
Governance
Azure Governance establishes the tooling needed to support cloud governance, compliance auditing, and automated guardrails.
Cost Management, exploring guidance to cost reporting controls.Finding the structure of tags that fits your costs and recharging model might help you track your cloud spend. Azure Hybrid benefits might help reducing the costs of licensing of your workloads.
Azure reservations helps save money by committing to one-year or three-year plans for multiple products. Azure savings plan for compute is Microsoft most flexible plan and can generates savings yup to 65 percent on pay-as-you-go-price.
Consider using Azure Policy to enforce tools (such as Microsoft Defender for Cloud, Disk Encryption, allow specific regions, resources, and skus.)
Security
This design area creates a foundation for security across your Azure, hybrid and multicloud environments.
Following the Zero Trust model, this a new security model that assumes breach and verifies each request as though originated from uncontrolled network.
I won’t to go depth in this session, as the next posts will be more specific about identity, network, data, and workloads protection.
Mangement
This session is a foundation for operations management across your workloads placed on Azure.
Operations baselines such as Inventory and visibility, compliance, and protect&recover are covered for this session.
Next Post
The next post will cover Identity and Access control, the idea is covering the tooling and the practical approach for this subject.
For this sequence of posts, I’ll be using the Defense-in-Depth approach as a guiding principle. Defense in Depth is strategy that leverages multiples security measures to protect an organization’s assets. In case one line of defense is compromised, additional layers exist as a backup to ensure that threats are stopped along the way.
Links
Azure Well-Architected Framework
Leave a Reply